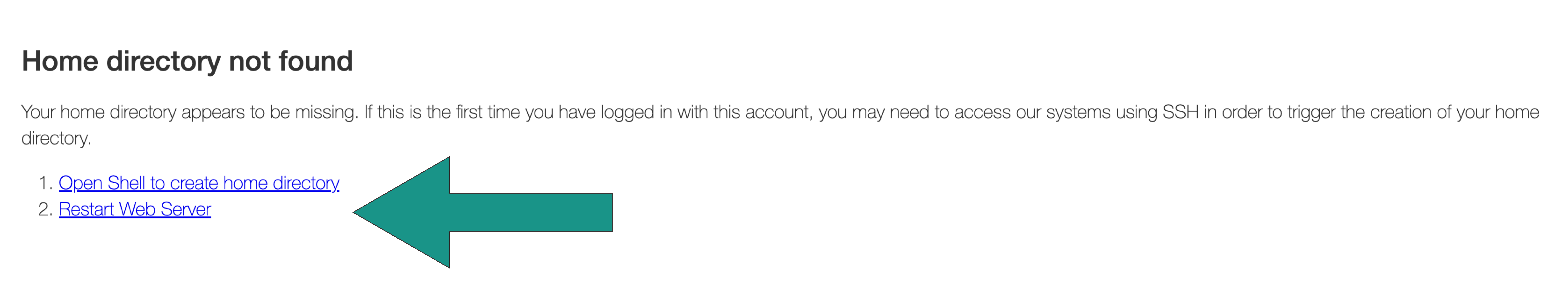
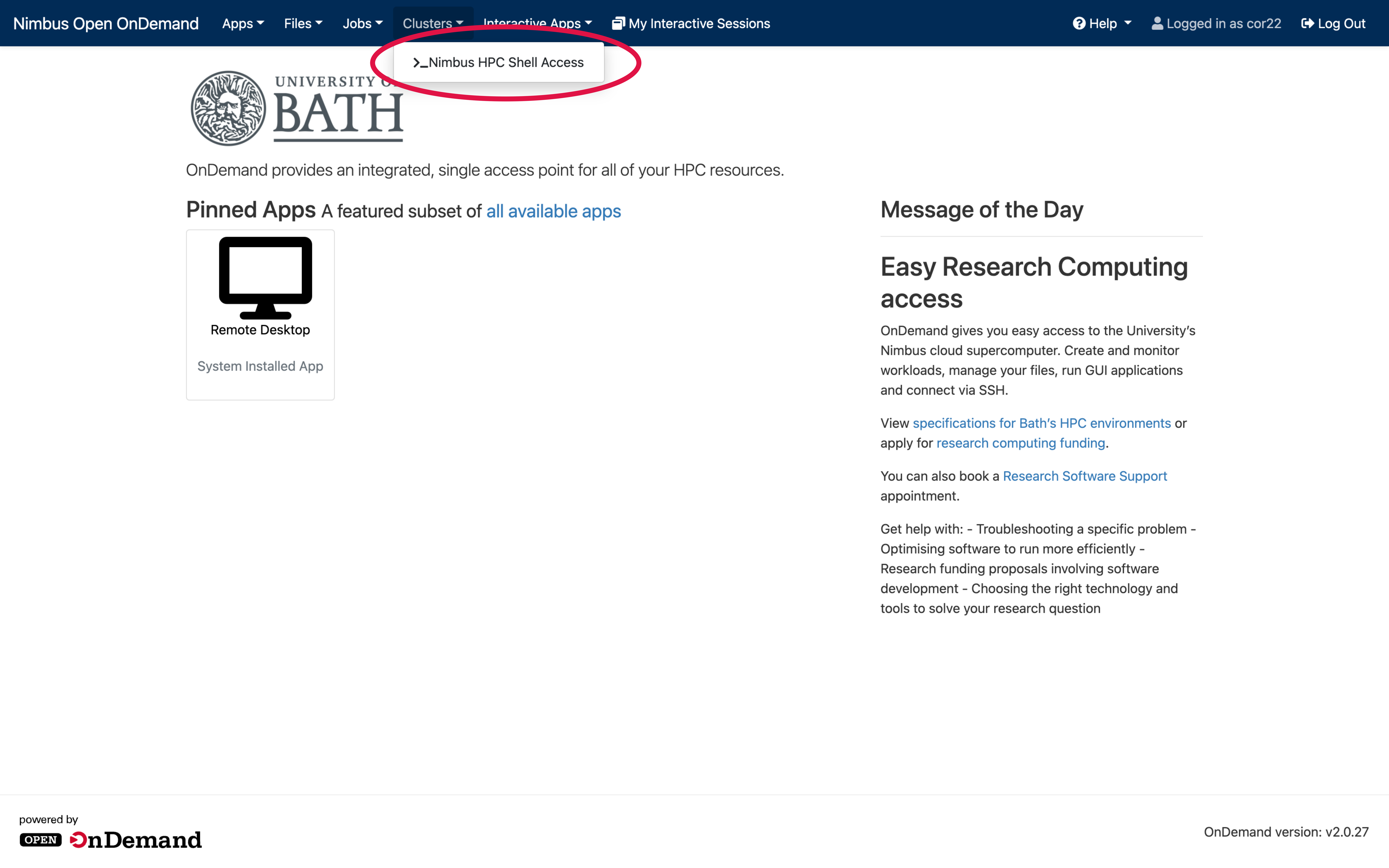
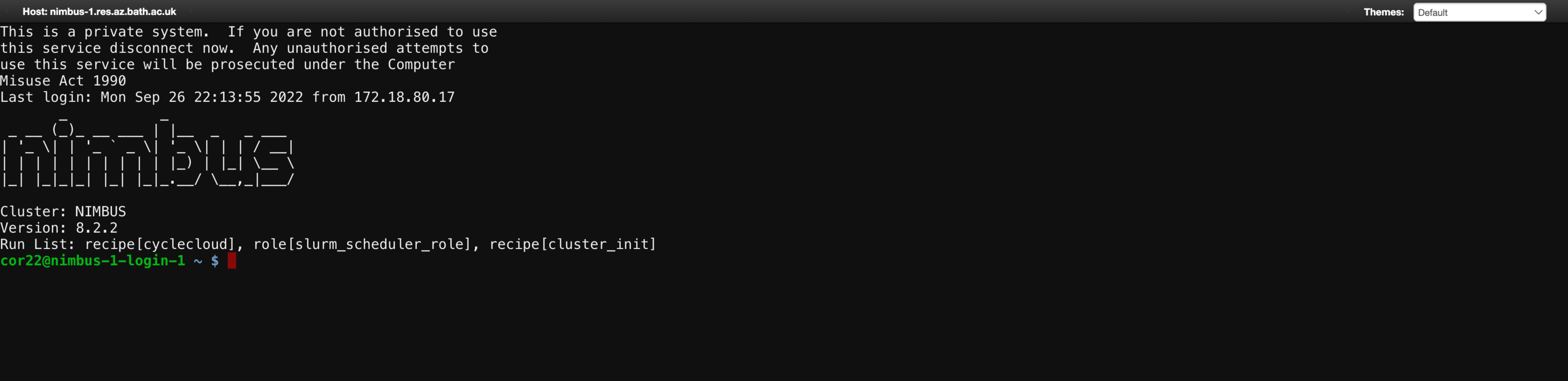
SSH
As HPC services are remote machines, interaction is done over an encrypted communication channel called Secure Shell version 2 (SSH-2). This allows command-line access to one of the login nodes of a HPC service, from which you can run commands or use a command-line text editor to edit files.
Security¶
Users and system operators have a shared responsibility to ensure the security of resources. System operators monitor the system, ensure security patches are up-to-date and that the systems is configured to restrict access correctly e.g. so that users cannot see each others data/files by default.
Users should follow best practice to mitigate the risk of accounts and access details being compromised, e.g. we all know that we must keep our passwords secret. You shouldn't make your files accessible to others unless necessary.
Strong passwords¶
A strong password describes a password that is difficult to detect by both humans and computer programs, effectively protecting data from unauthorized access. A strong password consists of at least twelve characters (and the more characters, the stronger the password) that are a combination of letters, numbers and symbols (@, !, &, ^ etc) if allowed. Passwords are typically case-sensitive, so a strong password contains letters in both uppercase and lowercase. Strong passwords also do not contain words that can be found in a dictionary or parts of the user's own name.
SSH key pairs¶
An alternative to using a password is to use an ssh key-pair. A public key pair consists of two parts, a public part and a private part which are related. One is used to lock the message the other is used to unlock the message:
- The public part is used to lock (encrypt) the message so that it can be sent over the internet and can be shared.
- The private part is used to unlock (decrpyt) the message and should not be shared.
Set up a key pair¶
The SSH key pair consists of a private part and a public part. The public key can be put on remote machines to allow you to log-in without the use of a password. You keep the private part of the key secure on your local machine protected with a passphrase.
Public key encryption uses fancy maths to enable secure communication over an open channel. There are a number of methods the most common being RSA) which uses prime numbers. If you are going to use this you should use a key size of at least 2048 and preferably 4096. Public keys can be broken with brute force computation and the longer the key the more secure it is.
An alternative encryption method and the one we recommend you to use are based on EdDSA (Ed25519). For our purposes the key pair works in the same way. Your public key can go on the remote resource or service and the private key is kept protected on your local machine. You can generate a key pair with:
ssh-keygen -o -a 100 -t ed25519
- ssh-keygen is the command to generate the key pair
- -o specifies to use a strong format to save the key
- -a 100 increases the strength of encryption with your passphrase
- -t ed25519 specifies the encryption method used
When you create a SSH key pair you will be prompted to provide a passphrase. This is effectively password for your private key and like a password should be kept secret. Now when you try to use the key, you should be asked for your key pair passphase (which you entered when you created the key pair) rather than your remote machine password.
Access to the HPC cloud service can be through key pairs, but ensure your key pair is protected by a passphrase.
More details on ssh and security¶
For further details on ssh, and security you can visit the Research Computing lesson:
https://arc-lessons.github.io/security/00_schedule.html